What is cyber threat intelligence (CTI)?
According to the SANS Institute, the analysis of an adversary's intent, opportunity, and capability to do harm is known as cyber threat intelligence. Cyber threat intelligence thus represents a force multiplier for organizations looking to establish or update their response and detection programs to deal with increasingly sophisticated threats.
About cyber threat intelligence
With cyber threats becoming more evasive in design and adversaries growing more persistent and adept in exploiting vulnerabilities and other loopholes, the importance of cyber threat intelligence only continues to grow. Both security teams and vendors alike are expanding the collection of evidence-based knowledge (e.g., context, mechanisms, indicators, implications, and action-oriented advice) about existing or emerging menaces or hazards to assets. CISOs should plan for current threats, as well as those that could emerge in the long term. the power of cyber threat intelligence to understand the nature of today’s advanced threats and how attackers target various organizations.
Why is CTI Important?
Cyber Threat Intelligence represents invaluable security information, which can be acted upon to improve threat visibility, detection and response actions. It is derived from the analysis and classification (malicious or benign) of various threat artifacts like files, URLs, and email & web-borne threats. Threat intelligence is the big picture of who is attacking you, which methods (attack steps, tools, delivery mechanisms, etc.) are being used and what is being targeted (data, user, infrastructure).
Applying the right threat intelligence not only improves security effectiveness but also brings in the much-needed predictability against today’s modern adversaries and tomorrow’s threats. There are various ways to source threat intelligence, and organizations can consider both internal as well as external sources as per their security needs. By leveraging threat intelligence, organizations can make informed security decisions to identify and mitigate various cyber risks that can disrupt business operations, impact the bottom line and damage organizational reputation.
What Issues Does Cyber Threat Intelligence Address?
There are several reasons why CTI is trending as the chartbuster theme among other contemporary cybersecurity discussions like Managed Detection and Response (MDR).
Digital Transformation
The rapid disappearance of the perimeter-based approach to enterprise security, which continued as the default method for many years until the broader adoption of cloud computing came around and started to tear down the familiar security posture linked with the perimeter-driven security practices. Accelerated digital transformation in the aftermath of the Covid pandemic further compounded this challenge. As a result, this unprecedented transition inevitably required security vendors, SaaS & cloud platforms, and enterprise security teams to rethink their strategy for a better security posture.
Sophisticated Threat Landscape
The threat landscape as it stands today is much more challenging and complex, largely because the attack surface has expanded like never before. An attacker has so many means and ways to target an organizational network – detecting unpatched systems and flying under the radar, compromising an endpoint with a ransomware attack, exploiting zero-day (not known to anyone) vulnerabilities in security systems, IT or cloud applications, or operating systems to bypass the prevention layer, launching targeted social engineering attacks like spear-phishing and Business Email Compromise (BEC), abusing legitimate processes (e.g., Windows PowerShell) to remain undetected while being able to exfiltrate mission-critical data from the target network and more. Without the right threat intelligence, it is impossible to gain the required understanding of these attack methods and threat actor behaviour. Cybersecurity professionals like threat hunters and researchers refer to this security intelligence as the “TTPs,” meaning the techniques, tactics and procedures attackers use to develop and deliver advanced cyber threats.
Evolving Methods and Tools
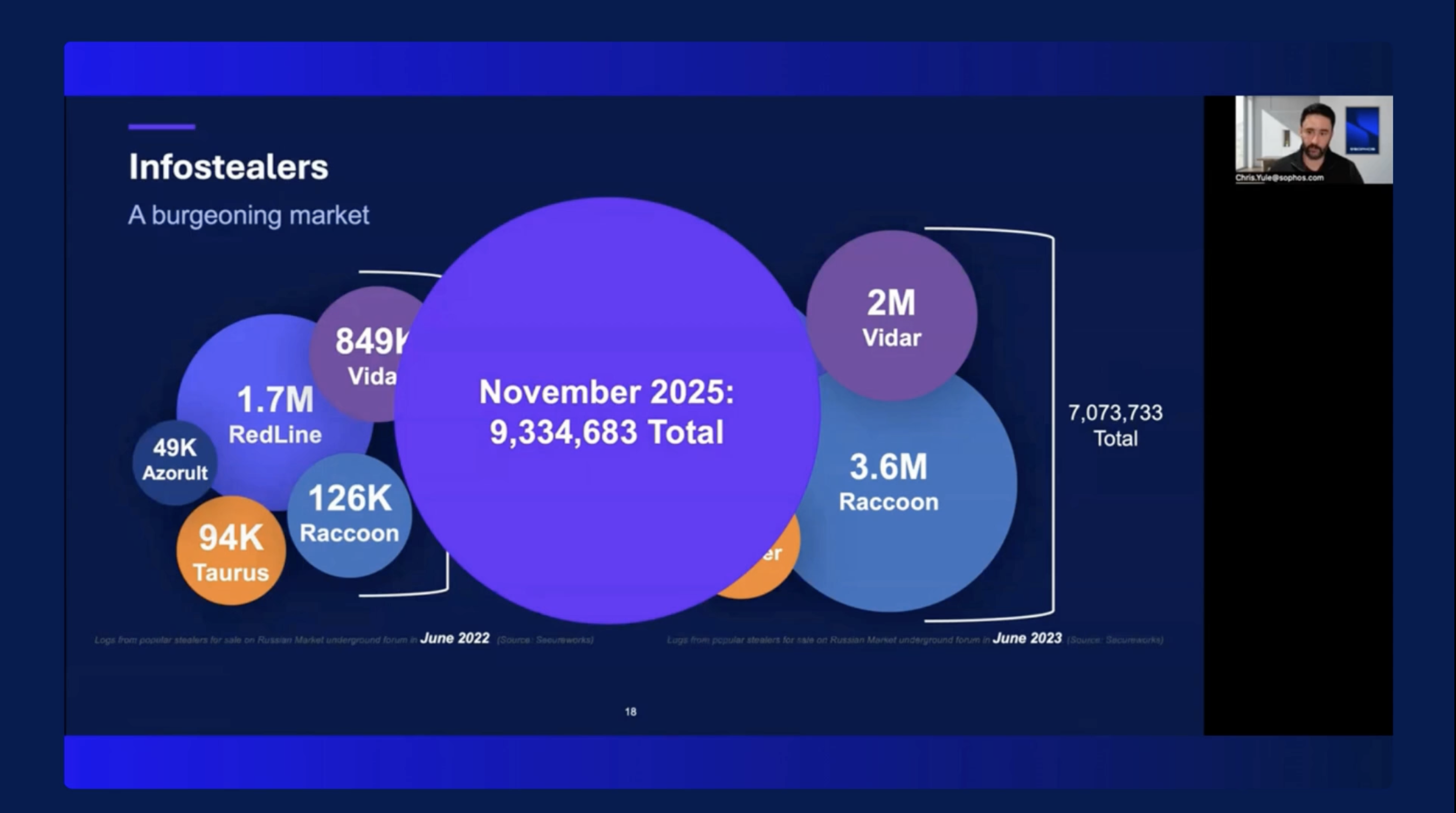
Cybercriminals have an increasingly large number of methods and tools at their disposal. Findings from the latest Sophos Threat Report reveal the increasing commercialization of cybercrime, which is giving birth to a thriving “Cybercrime-as-a-Service” industry and ecosystem. Today’s modern attackers are continuously devising innovative methods and have access to other adversaries that provide limitless resources to design and launch advanced threats using targeted attacks. No wonder security teams that rely on just firewalls, endpoints and other point products cannot detect or thwart such evolved malicious activities.
Cyber threat intelligence provides organizations and security vendors with an adversary-focused additional layer of defense, which helps speed up detection and response actions against threats that matter. With the right and comprehensive Cyber Threat Intelligence (CTI), defenders can understand how the attackers manage to succeed, the steps they follow, their motivation, and the various tools and methods they use to hit their targets. Threat intelligence is now vital in improving security effectiveness and in detecting and preventing innovative threats from modern attackers.
Analyst Fatigue
The growing volume of alerts emerging from multiple security systems which are adding to analyst fatigue and poor visibility into what really matters. Security teams should be spending time detecting and eliminating threats, but as they are inundated by large amounts of raw data and false positives, they miss out on the threats that need to be prevented before they turn into a data breach. Acting with the right speed and accuracy are critical aspects in spotting threats that are targeting businesses. With the right threat intelligence, organizations gain much-needed context (visibility as well as understanding) into the “who, what and why” of the threats they are facing. It’s like saying, “This room is full of threats,” vs. “These people in the room are the threats that need to be nabbed.”
IT Infrastructure
As MITRE explains, “analysis and tailoring of CTI and establishing context enables the SOC to prioritize the actions of detection and prevention to conserve resources, honing the effectiveness of SOC operations.” Security teams, when armed with threat context, gain the ability to separate vital threat signals from noise (large volume of alerts).
Building and maintaining such an infrastructure to detect, analyze and scope emerging and unknown threats and then continuously improving the findings from this research can be a daunting and arduous task for most security teams. This is a key reason why both security vendors and enterprise security teams turn to expert providers of threat intelligence services and solutions. With the right threat classification, accuracy of threat data and context-enriched security information, defenders can fine-tune existing security controls and build effective security mechanisms to respond better against ever-evolving cyber threats and modern attackers.
How does Sophos help with cyber threat intelligence?
From pioneering the vision of “Synchronized Security,” which brought together Network, Endpoint, Email, Mobile, Wi-Fi and Encryption security solutions in a connected cybersecurity ecosystem, with all sharing security intelligence in real-time, to launching Adaptive Cybersecurity Ecosystem (ACE), which leverages automation and expert analysts to create protection that continuously learns and improves, Sophos has made notable contributions to threat-intelligence driven cybersecurity innovations.
More recently, Sophos announced ‘X-Ops’ intelligence unit, which has consolidated three previously separate units – SophosLabs, Sophos SecOps and Sophos AI – into one cohesive group, to combat advanced cyberattacks quickly and with greater accuracy. Sophos brings the power of 30-plus years of rich experience in threat analysis and research, and X-Ops intelligence is used in Sophos’ entire portfolio of Network, Endpoint and Cloud security solutions and MDR services.
What makes Sophos cyber threat intelligence unique?
- Sophos' approach to threat intelligence is based on three key aspects - accuracy, relevancy, and timeliness. This ensures that Sophos customers get the latest and most reliable protection against threats specific to their organizations.
- With its extensive expertise spanning Network, Endpoint, Email, Web and Cloud cybersecurity, Sophos delivers multi-vector cyber threat intelligence, bringing insights from a wide attack surface. Every day, Sophos analyses millions and billions of threat artifacts, including URLs, web pages, IP addresses, file hashes, emails, and more. This way, Sophos is able to extract meaningful security intelligence from the latest malicious campaigns and attack methods, being able to deliver continuously updated defense against the latest threat trends like malicious URLs & websites, ransomware, zero-day and sandbox-aware malware, Business Email Compromise (BEC) and spear phishing attacks.
- Sophos constantly enhances human-led threat intelligence with powerful automation, curation and AI innovations, delivering truly multi-layered and high-fidelity cyber threat intelligence against both known as well as never-before-seen cyber threats.
- To help the worldwide community of cloud developers and OEM security partners, Sophos has developed Intelix, a cloud-based threat intelligence and threat analysis platform. SophosLabs Intelix provides detailed and explainable threat intelligence with deep analysis for known clean and malicious objects, including files, web pages, and IP addresses.
- Sophos leads by example in supporting industry collaboration and security community initiatives on cyber threat intelligence, including collaborations with ReversingLabs and supporting Information Sharing and Analysis Organization (ISAO) organizations.
- Sophos threat intelligence not only helps enrich and understand the Indicators of Compromise (IOCs) better, but also provides deeper and quicker insights into the Indicators of Attacks (IOAs). Simply put, with Sophos threat intelligence, security teams can not only enhance the forensic evidence of cyberattacks (file hashes, URLs, etc.) but can also effectively monitor, detect and thwart active attacks (signs like lateral movement, credential exploitation, outbound command-and-control or C&C communications). See this MITRE ATT&CK matrix to understand various tactics and stages of cyber attacks from the mind of a modern adversary.
OEM Threat Intelligence Solutions from Sophos
If you are a security vendor or an enterprise security team, requiring external threat intelligence to either supplement or enhance your security solutions and infrastructure, contact the Sophos OEM team to find the right solution for your use case.
Sophos provides modular, extensible, and contextual threat intelligence to OEM security partners to help them deliver better cybersecurity for the most demanding use cases including:
- Web and Email Security
- File Analysis
- URL Classification
- Sandboxing
- Phishing, Spear phishing and BEC prevention
- DLP
Download the datasheet for OEM threat intelligence solutions.
Related security topic: What is cloud workload protection?
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)