Sophos, a global leader in next-generation cybersecurity, today published a SophosLabs article, Following the Money in a Massive “Sextortion” Spam Scheme, that shows how the funds extracted from victims led to an underbelly of cybercriminal activity. Researchers traced the origin of millions of sextortion spam emails launched between September 2019 and February 2020 and then analysed what happened to the money deposited by victims in attackers’ bitcoin wallets. The bitcoin extorted from the scams totalled approximately $500,000. SophosLabs believes this report is the first to trace a bitcoin haul from sextortion.
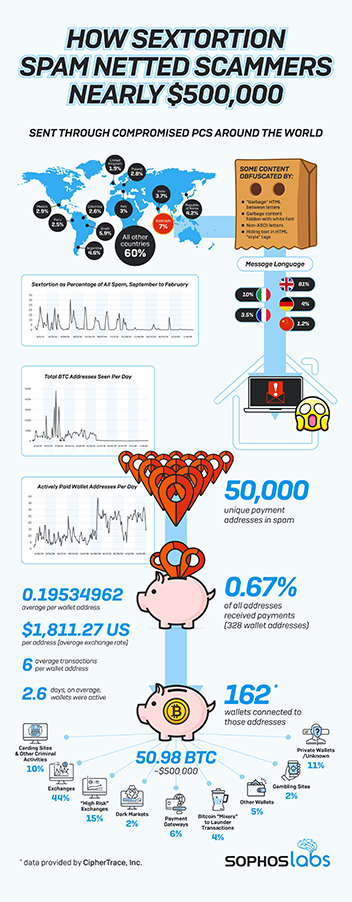
Sextortion is a widely used form of spam attack that accuses the recipient of visiting a pornographic website and threatens to share video evidence with their friends and family unless the recipient pays. In the examples analysed, recipients were asked to pay up to $800 in bitcoin into designated wallet addresses.
SophosLabs researchers worked with CipherTrace to track the flow of the money from these wallets. They found that the extorted funds were used to support subsequent illicit activity, such as transacting with dark web marketplaces and buying stolen credit card data. Other funds were quickly moved through a series of wallet addresses to be consolidated, put through “mixers” in an attempt to launder the transactions or converted to cash.
“The cybercriminal underworld is an intricate web and SophosLabs’ research shows how attackers used the money raised in one operation to invest in another,” said Tamás Kocsír, a security researcher at SophosLabs who led the research. “Sextortion scams prey on fear and this makes them an effective way of making quick money. Across the five months of our investigation we saw wave after wave of attacks, often taking place over the weekend and sometimes accounting for up to a fifth of all spam tracked at SophosLabs. And while most recipients either didn’t open the email or didn’t pay, enough of them did to net the attackers around 50.9 bitcoin, equivalent to nearly $500,000.”
The scams exploited global botnets on compromised PCs to dispatch millions of spam emails to recipients around the world. Vietnam, Brazil, Argentina, the Republic of Korea, India, Italy, Mexico, Poland, Colombia, and Peru are the top 10 countries where these compromised computers were used to dispatch the spam messages, of which 81% were in English, 10% were in Italian, 4% were in German, 3.5% were in French, and 1.2% were in Chinese.
“Spam campaigns are relatively cheap and easy to implement, but the assumption that this means they are launched only by low-skilled, opportunistic attackers could be inaccurate,” said Kocsír. “Our research found that some of the scam emails featured innovative obfuscation techniques designed to bypass anti-spam filters. Examples of this include breaking up the words with invisible random strings, inserting blocks of white garbage text, or adding words in the Cyrillic alphabet to confuse machine scanning. These are not beginner techniques and they are a good reminder that spam attacks of any kind should be taken seriously. A robust approach to cybersecurity is essential. If you are worried about becoming the target of a sextortion scam, disable or cover the camera on your computer.”
For additional information, please reference the SophosLabs Uncut article.
For additional perspective on this story go to Naked Security.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
