
Looking to Compare Sophos with Microsoft?
Prevent Breaches, Ransomware, and Data Loss with Sophos

Organizations that implement Microsoft Defender often prioritize cost. However, Microsoft Defender's extensive manual configuration, testing, and tuning can increase its total cost of ownership. Sophos provides superior cyber protection with a best-practice configuration out of the box, centralized management, and more.
Sophos vs. Microsoft
| FEATURES | Sophos | Microsoft |
|---|---|---|
| Attack Surface, Pre- and Post-Execution | ||
| Attack surface reduction, with multiple technologies for web protection, application control, and device control that eliminate attack vectors and protect against data loss | Partially provided | |
| Defenses that automatically adapt to human-led attacks | Partially provided | |
| Automated Account Health Check to maintain a strong security posture | ||
| Security Heartbeat to share health and threat intelligence information between multiple products | Partially provided | |
| Exploit Mitigations | ||
| Mitigations enabled by default in Windows operating system | 7 | 7 |
| Mitigations enabled by default in product | 60 | 0 |
| Mitigations off by default requiring manual configuration | 0 | 32 |
| Ransomware detection with automatic document rollback | Partially provided | |
| Remote ransomware blocking and rollback | Not provided | |
| Feature parity across Windows, macOS, and Linux | Partially provided | Partially provided |
| Management, Investigation, and Remediation | ||
| Single management console for managing and reporting | Not provided | |
| Alert triage and assistance | ||
| Extensive threat-hunting and investigation capabilities | ||
| Suitable for customers without an in-house SOC | Partially provided | |
| Suitable for large enterprise organizations with a full in-house SOC | ||
| Threat Hunting and Response | ||
| Endpoint detection and response (EDR) functionality | (E5 required) | |
| Integrated extended detection and response (XDR) enables analysts to hunt for and respond to threats across your environment, correlate information, and pivot between endpoint, server, network, mobile, email, public cloud, and Microsoft 365 data | (E5 required) | |
| MDR service provides 24/7 threat hunting, detection, and unlimited remediation to organizations of all sizes, with support available over the phone or through email | ||
| Incident reponse included in top MDR tier | (Optional IR Retainer for lower MDR tiers) | Not provided |
| Integration with third-party security controls to leverage your existing security investments and provide full visibility into your environment and detections and alerts to your team and the MDR team | (Requires additional purchase | |
| Encrypted network traffic analysis (NDR) | Not provided | |
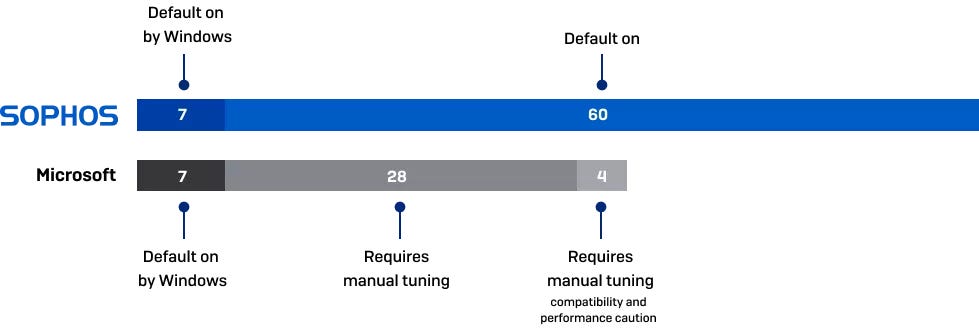
Default Exploit Prevention
Straight out of the box, Sophos builds on top of the basic protection offered by Windows, with an additional 60 preconfigured, tuned, and automatically enabled exploit mitigations. With Microsoft, you must manually activate and tune the mitigations, increasing the risk of misconfiguration or thinking you're protected when you're not.

Adaptive Attack Protection is a dynamic step up in endpoint security. When a hands-on-keyboard attack is detected, Sophos Endpoint automatically activates extra defenses with a "shields up" perspective. It stops an attacker and provides you with plenty of time to respond. For more information, watch the Adaptive Attack Protection video.

Consolidate your defenses by integrating your endpoint, server, network, mobile, cloud security, and third-party security controls into the Sophos Adaptive Cybersecurity Ecosystem. All Sophos products are continuously optimized with real-time threat intelligence and operational insights from Sophos X-Ops.

.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
