Security and Compliance at the Pace of DevOps
Prevent security breaches that exploit vulnerabilities and resource misconfigurations pre-deployment with Cloud Optix. Seamlessly integrate Sophos security and compliance checks at any stage of the development pipeline.
Enable Fast and Secure Development
The rise in the adoption of Kubernetes, Docker services, and DevOps methodologies have all allowed organizations to dramatically increase their agility, enabling development teams to automate provisioning of cloud infrastructure and put new versions of software live quickly.
To enable that transformation, security professionals must support DevOps teams with a “Shift Left” approach – providing integrated security and compliance tools that work with existing processes to enable fast and secure delivery.
Prevent Security Breaches with DevSecOps
Cloud Optix DevSecOps tools work seamlessly with existing DevOps processes to help prevent security breaches pre-deployment. Cloud Optix ensures container images and Infrastructure-as-Code (IaC) templates containing insecure configurations as well as embedded secrets and keys never make it to a test or live production environment.
Enabling a “Shift Left” Approach
Container Image Scanning
Scan container images in ECR, ACR, Docker Hub registries, as well as GitHub and Bitbucket IaC environments to identify operating system vulnerabilities and fixes to prevent threats pre-deployment.
Infrastructure-as-Code Scanning
Automatically detect misconfigurations, embedded secrets, passwords, and keys in Terraform, AWS CloudFormation, Ansible, Kubernetes, and Azure Resource Manager (ARM) template files.
Integrate via API
Seamlessly integrate with GitHub and Bitbucket early on to receive on-demand scan results in the Cloud Optix console, or use the REST API to scan IAC templates and container images at any stage of development.
Drift Detection and Guardrails
Continuously monitor and detect drift in configuration standards, and prevent, detect, and automatically remediate accidental or malicious changes in resource configuration before they are compromised.
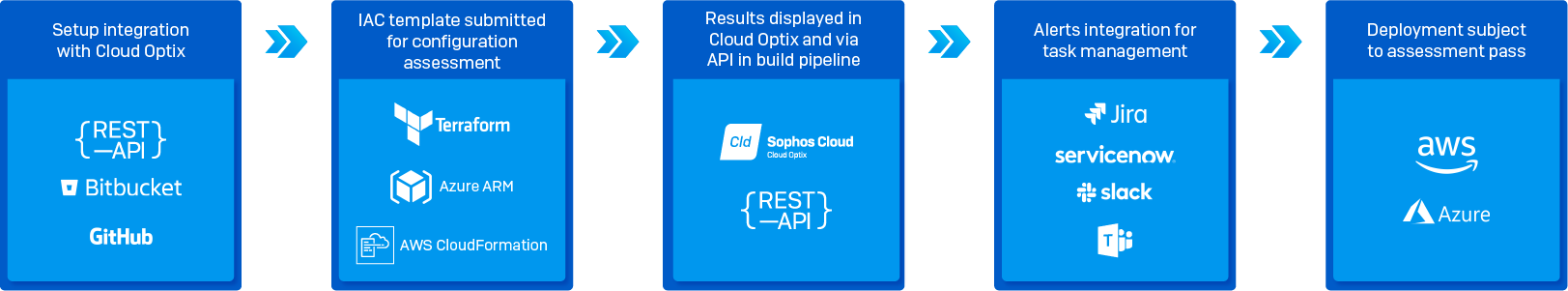
How Cloud Optix Works
Block vulnerabilities pre-deployment with Cloud Optix container image and Infrastructure-as-Code template scans.
IAC Template Scanning Configuration Vulnerabilities

Container Image Scanning Operating System Vulnerabilities
Calculate the ROI of DevSecOps
Half a day can easily be consumed by development teams coding automated pipeline testing scripts for each cloud account. With Cloud Optix DevSecOps security and compliance scanning tools, you can achieve considerable time savings.