.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Sophos Endpoint
Prevent breaches, ransomware, and data loss with AI-powered endpoint security
Sophos Endpoint delivers unparalleled defense against advanced cyberattacks with award-winning endpoint protection and control. A prevention-first approach stops the broadest range of threats quickly before they impact your endpoints and servers. Powerful detection and response functionality (EDR) lets your organization hunt for, investigate, and respond to suspicious activity and evasive threats.
Sophos has time and time again proven to be one of the most effective endpoint security platforms we have encountered, reliably performing and disrupting attackers at a level that simply outperforms the majority of the players in the next-generation antivirus and endpoint detection and response (EDR) space.
Jon Miller, CEO and co-founder of Halcyon



Sophos named a Leader in the 2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
Safeguarding your digital assets has never been more critical

Evolving threats

Complexity is the enemy of security

Reactive responses
IT teams are on the back foot, responding to threats only after they’ve caused the damage rather than stopping them earlier in the attack chain.


A 2026 Gartner® Peer Insights ™ Customers’ Choice for Endpoint Protection Platforms
Sophos has been recognized as a Customers’ Choice vendor in the 2026 Voice of the Customer report for Endpoint Protection Platforms with a 4.9/5.0 overall rating based on 286 total reviews as of 30 November 2025

OVERVIEW
AI-powered, prevention-first approach
Sophos Endpoint takes a comprehensive, prevention-first approach to security, automatically blocking threats without relying on any single technique. Deep learning AI models protect against known and novel attacks. Web, application, and peripheral controls reduce your threat surface and block common attack vectors. Behavorial analysis, anti-ransomware, anti-exploitation, and other advanced technologies stop threats fast before they escalate, so resource-stretched IT teams have fewer incidents to investigate and resolve.

Sophisticated technologies block the broadest range of attacks.

Easy to deploy and identify drifts in security posture, with strong protection enabled by default.

Top-rated protection with industry-leading results in third-party testing.
Airtight ransomware protection
Robust defense against remote ransomware
According to Microsoft's 2024 Digital Defense Report
Sophos Endpoint is the industry’s most robust zero-touch endpoint defense against remote ransomware, thanks to our universal proprietary CryptoGuard technology.
Adaptive Attack Protection
Critical Attack Warning
Extend your protection to the workspace
Sophos Workspace Protection extends protection to your apps, data, and remote and hybrid workers easily and affordably. Provide secure zero-trust connectivity, safe web browsing, data boundary controls, and insights into email threats.

Easy to set up and manage
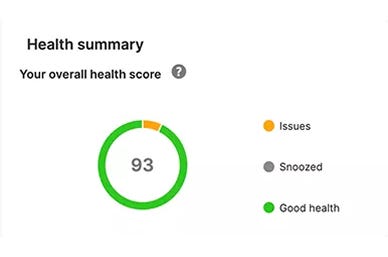
Account health check
Poorly configured policy settings, exclusions, and other factors can compromise your security posture. The account health check feature identifies security posture drift and high-risk misconfigurations, enabling administrators to remediate issues with one click.
Protect all your endpoints
Get complete protection across all your desktops, laptops, servers, tablets, and mobile devices. Sophos Endpoint supports all major operating systems, including legacy platforms for critical systems.
The industry's most sophisticated endpoint security solution
Mitigate the risk of threats
Stopping attacks early is less resource-intensive than monitoring and remediating them later in the attack chain. Intercepting network traffic on the endpoint provides powerful protection benefits for users both on and off the company network. Solutions that lack this full range of threat surface reduction capabilities have less opportunity to block attacks before they penetrate your systems.
Web Protection
Web Protection intercepts outbound browser connections and blocks traffic destined for malicious or suspicious websites. It stops threats at the delivery stage by preventing users from being diverted to malware delivery or phishing websites.
Web Control
Web Control uses the same traffic interception technology, enabling you to block access to undesirable or inappropriate content, such as adult and gambling websites.
Application Control
Application Control enables you to block applications that may be vulnerable, unsuitable for your environment, or that could be used for nefarious purposes. Sophos provides pre-defined categories to block or monitor apps, removing the burden of blocking individual applications by hash.
Peripheral (Device) Control
Peripheral (Device) Control enables you to monitor and block access to removable media, Bluetooth, and mobile devices to prevent certain hardware from connecting to your network.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) monitors and restricts the transfer of files containing sensitive data. For example, prevent employees from sending confidential files home using web-based email.
Download Reputation
Download Reputation analyzes files as they’re downloaded and uses SophosLabs global threat intelligence to provide a verdict based on prevalence, age, and source, prompting users to block files with low or unknown reputation.
Automatically stop threats
Stopping more threats early in the attack chain enables you to focus on investigating fewer incidents. Some detection and response solutions focus on collecting telemetry for investigation at the expense of providing comprehensive prevention, to maintain a reduced agent footprint. Sophos delivers broader threat prevention capabilities, with efficacy validated through consistent top scores in independent tests.
Deep learning (AI-powered) malware prevention
Deep learning (AI-powered) malware prevention analyzes binaries to make decisions based on file attributes and predictive reasoning. Deep learning is an advanced form of machine learning that detects and blocks malware, including new and previously unseen threats.
Anti-Exploitation
Anti-Exploitation guards process integrity by hardening application memory and applying runtime code execution guardrails. Over 60 anti-exploitation techniques in Sophos Endpoint are enabled by default, require no training nor tuning, and extend far beyond the protections provided by the native Windows OS or most other endpoint security solutions.
Some vendors including Carbon Black, SentinelOne and Microsoft lack extensive exploit mitigations or require significant manual tuning.
Behavior Analysis
Behavior Analysis monitors process, file, and registry events over time to detect and stop malicious behaviors and processes. It also performs memory scanning, inspects running processes to detect malicious code only revealed during process execution, and detects attackers implanting malicious code in the memory of a running process to evade detection.
Antimalware Scan Interface (AMSI)
Antimalware Scan Interface (AMSI) determines whether scripts (e.g., PowerShell or Office macros) are safe, including if they are obfuscated or generated at runtime, blocking fileless attacks where malware is loaded directly from memory. Sophos also has a proprietary mitigation against malware that attempts to evade AMSI detection.
Live Protection
Live Protection extends Sophos’ comprehensive on-device protection with real-time lookups to SophosLabs' latest global threat intelligence for additional file context, decision verification, false positive suppression, and file reputation. Our Tier 1 threat research provides additional live intelligence from Sophos’ expansive product portfolio and global customer base.
Some vendors including Carbon Black, CrowdStrike, and SentinelOne rely solely on pre-trained machine learning models.
Malicious Traffic Detection
Malicious Traffic Detection detects a device attempting to communicate with a command and control (C2) server by intercepting traffic from non-browser processes and analyzing whether it is destined for a malicious address.
Application Lockdown
Application Lockdown prevents browser and application misuse by blocking actions not commonly associated with those processes. For example, a web browser or Office application attempting to launch PowerShell.
RELATED PRODUCTS AND SERVICES
Cybersecurity for all your needs
Sophos Endpoint Detection and Response (EDR)
Sophos Endpoint is included in Sophos EDR. Elevate your endpoint defenses with detection and response tools.
- Gain insights into evasive threats across your endpoints and servers.
- Includes powerful capabilities for IT operations and security analysts.
- Single agent for endpoint protection, detection, and response.
- Contain threats with accelerated and automated response tools.
- Multi-platform, multi-OS support.
Sophos Extended Detection and Response (XDR)
Sophos EDR is included in Sophos XDR: Empower your security team to defend against sophisticated multi-stage, multi-vector attacks with extended detection and response (XDR) tools.
- Accelerate investigation and response with AI-powered tools.
- Complete visibility across all key attack vectors.
- Integrate existing security and IT tools to detect and neutralize attacks.
- Leverage a fully integrated portfolio of Sophos products.
- Rapidly contain and remediate threats.
- Includes Sophos Endpoint and Sophos EDR.
Sophos Managed Detection and Response (MDR)
Free up IT and security staff to focus on business enablement and leverage superior security outcomes delivered as a service.
- Instant security operations center (SOC).
- 24/7 threat detection and response.
- Expert-led threat hunting.
- Full-scale incident response capabilities.
- Keep the cybersecurity software you already have.
- The most robust MDR service for Microsoft environments.
- Breach protection warranty.
.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Try Sophos Endpoint for free
We offer the world's best endpoint protection.
With Sophos Endpoint, you can:
- Access endpoint security that stops the broadest range of threats before they impact your systems and allows you to hunt, investigate, and respond to suspicious activity and indicators of attack.
- Automated responses to threats including automatic file rollback after encryption by ransomware and defenses that automatically adapt to the context of an attack.
- Use the Sophos Central cloud-based management platform to manage, view detections and alerts, investigate and remediate potential threats, and more across all Sophos products.
Get Started Today
Sign up for a free, no-obligation 30-day trial of Sophos Endpoint.
If you have an active Sophos Central account, you can sign up for a free trial of Sophos Endpoint and Sophos XDR from the Sophos Central Admin Console. To do so, log in to Sophos Central, then select "Free Trials," followed by "Sophos Endpoint Advanced with XDR."

See why customers choose Sophos

A Leader in the 2024 IDC MarketScape for Modern Endpoint Security for Small and Midsize Businesses

A Leader in the Gartner 2025 Magic Quadrant for Endpoint Protection Platforms for the 16th consecutive time

A Leader for Endpoint Protection Platforms in the G2 Winter 2026 Reports

Industry-leading protection verified by independent third-party testing
Sophos State of Ransomware 2025 Report
How likely are you to be hit by ransomware? How many of your computers would be affected? Find these answers and much more in the Sophos State of Ransomware 2025 Report.
Customer Success
Already a customer? Find additional information to inspire, grow your knowledge, troubleshoot, and get help.
Frequently asked questions
Sophos Endpoint is a robust cybersecurity solution designed to protect your endpoint devices. It offers a prevention-first approach with advanced protection against ransomware, adaptive defenses, strong default policies, and ease of management.
Protection is Sophos Endpoint's core value proposition rather than an ancillary capability. Detecting an attack is not the same as protecting against an attack. The sooner you stop an attack, the less work there is, if any, to do later. Leveraging deep learning AI, strong controls, anti-ransomware, and anti-exploitation capabilities, Sophos Endpoint delivers real-time defense against a wide range of threats, ensuring business continuity and data integrity.
Organizations of all sizes and industries benefit from Sophos Endpoint’s protection-first approach. It is especially beneficial for businesses seeking to enhance their security posture against advanced endpoint security risks, including ransomware, zero-day exploits, and ever-evolving adversaries. Additionally, companies with limited in-house cybersecurity staff can leverage Sophos' Managed Detection and Response (MDR) service to free up staff and neutralize cyber threats 24/7/365.
The primary reasons organizations deploy Sophos Endpoint are to prevent breaches by helping to minimize the attack surface, protecting data against local and remote ransomware attacks, and minimizing the risk of data loss. Adaptive defenses are industry-first dynamic defenses that automate protection and adapt in response to active adversaries and hands-on-keyboard attacks. Sophos Central is a powerful, cloud-based cybersecurity management platform that unifies all Sophos next-gen security solutions and allows users to manage all your cybersecurity solutions from a single platform.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)