.avif?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Visibility, Governance, and Compliance
Detect and remediate multi-cloud security risks and maintain compliance.

Reduce Your Attack Surface

Multi-Cloud Security
Increase efficiency with cloud security posture management across AWS, Azure, and GCP environments in a single console.

Superior Visibility
See it All: Asset inventories, network visualizations, cloud spend, and configuration risk from development to production.

Continuous Compliance
Automate security best practice and compliance assessments and save weeks of effort with audit-ready reports.
Take It for a Test Drive
Instant access. No installation. No commitment.
Get Complete Visibility
We simplify asset discovery, monitoring, and network traffic visibility for AWS, Azure, and GCP.
- View on-demand asset inventories and exportable network topology visualizations.
- Stop shadow IT with automatic asset discovery and visualization of Sophos workload protection agent and firewall deployments.
- Prevent and remediate configuration risks across hosts, containers, Kubernetes environments, serverless, storage, database services, network security groups, and Infrastructure as Code (IaC) templates.
- Consolidate and simplify your security toolkit with one tool that also includes entitlements management and cloud spend monitoring.
Reduce Risk Without Losing Speed
Enable fast and secure development with integrated security configuration and compliance checks at any stage of the CI/CD pipeline.

Infrastructure-as-Code Scanning
Automatically detect misconfigurations, embedded secrets, passwords, and keys in Terraform, AWS CloudFormation, Ansible, Kubernetes, and Azure Resource Manager (ARM) template files.

Container Image Scanning
Prevent deployment of containers with operating system vulnerabilities and identify available fixes, with support for Amazon ECR, ACR, Docker Hub registries, IaC environments, and images in build pipelines.

Integrate via API

Drift Detection and Guardrails
Shift Left with Integrated Security Tools
IAC Template Scanning Configuration Vulnerabilities
Container Image Scanning Operating System Vulnerabilities

Maintain Cloud Compliance
Automate compliance and instantly access security best practice assessments and audit-ready reports.
Audit-Ready Reports
Monitor and manage security and compliance standards with custom or out-of-the-box templates and audit ready reports for FFIEC, GDPR, HIPAA, PCI DSS, SOC2, the CIS Foundations Benchmark, and other standards.
Reduce Your Audit Costs
Define what inventory items in your cloud account are subject to compliance standards and speed up your compliance audits.
Use with Your Existing Tools
Map Control IDs from RSA Archer, MetricStream, and other compliance tools you already use.
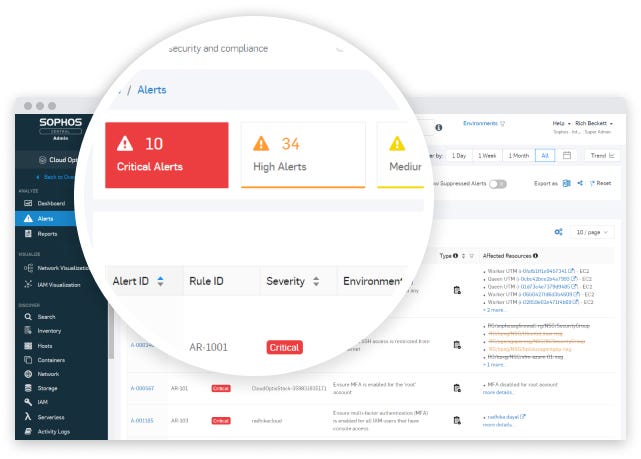
Minimize Time to Detect and Respond
Get a risk- assessed and prioritized view of your cloud security and compliance posture.
- Access risk-assessed and color-coded alerts that guide security teams to quick wins and critical security issues.
- Reduce alert fatigue with contextual alerts that group affected resources and provide detailed remediation steps.
- Automatically connect disparate actions with SophosAI to pinpoint malicious IAM role behaviors before they lead to breaches.
- Effortlessly assign alerts with JIRA and ServiceNow workflow management integrations.
Streamline SecOps and Improve Collaboration
Integrate with your SIEM, collaboration, and workflow management tools to increase agility across your organization.
Security Operations
Integrate with Splunk, Azure Sentinel, and PagerDuty to receive instant notification of security and compliance events.
Collaboration Tools
Instantly send and receive security alerts through Slack, Microsoft Teams, or the Amazon Simple Notification Service (SNS).
Workflow Management
Two-way integration lets you create JIRA and ServiceNow tickets in Sophos Central and embed alert response into your standard workflows.
Optimize Your Cloud Costs
Consolidate tools with security and cost monitoring in one solution to optimize AWS and Azure infrastructure costs and your security budget.
- Track cloud costs for multiple services side-by-side on a single screen to improve visibility and reduce wasted spend.
- Identify unusual activity indicative of abuse, highlighting top services contributing to spend with customizable alerts.
- Receive recommendations to optimize cloud provider spend, and integrate with AWS Trusted Advisor, and Azure Advisor services.
Extend Your Data Sources with XDR
Sophos Extended Detection and Response (XDR) provides cloud environment data, cross-platform detection capabilities, and deep insights and context into security issues.
- Use log data to search for evidence of malicious activity across AWS, Azure, APIs, and CLIs.
- Perform queries associated with attacker tactics to look for signs of initial access, persistence, and privilege escalation.
- Investigate hybrid cloud workload vulnerabilities and security incidents across your firewalls, endpoints, physical servers, emails, and more.
Take the Weight of Cloud Security Off Your Shoulders
- Deploy and manage Sophos protection from a single unified console.
- Sophos can connect you with an experienced Sophos Managed Security Partner.
- Sophos' Professional Services Team can help with initial deployment.
Respond to Security Incident at 3 a.m.
- Threat Hunting: Our elite team of threat analysts proactively hunts for threats and evaluates their potential impact and context.
- Response: Remotely disrupts, contains, and neutralizes the most sophisticated threats.
- Continuous Improvement: Get actionable advice for addressing the root cause of recurring incidents to stop them from occurring again.
Delivering Complete Multi-Cloud Security Coverage Across Environments, Workloads, and Identities

Visibility, Governance, and Compliance
View your multi-cloud environments to detect and remediate security risks, reduce your attack surface, and maintain compliance.
Cloud Workload Protection
Protect your infrastructure and data now and as it evolves with flexible host and container workload security for Windows and Linux.
Entitlements Management
Implement lead privilege across your multi-cloud environments and manage your identities before they're exploited.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
